Enhancing Transparency: The Impact of Integrated Character Codes on Securities Trading
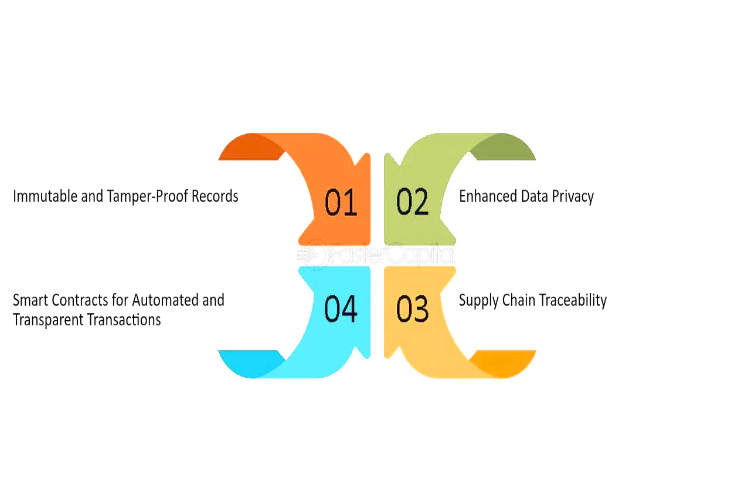
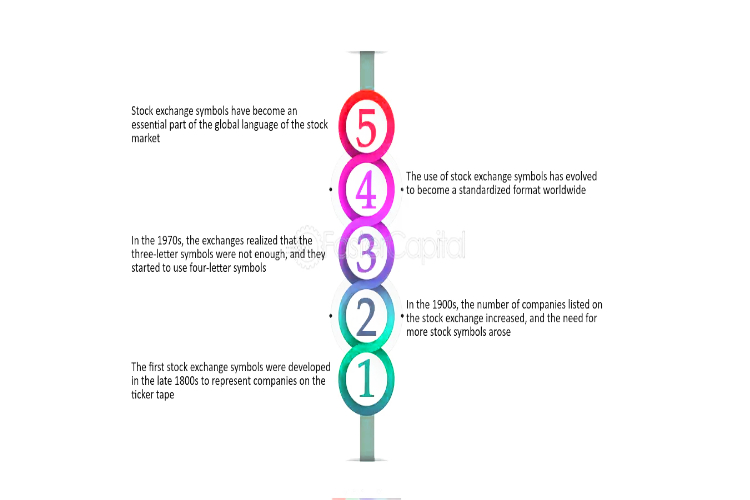
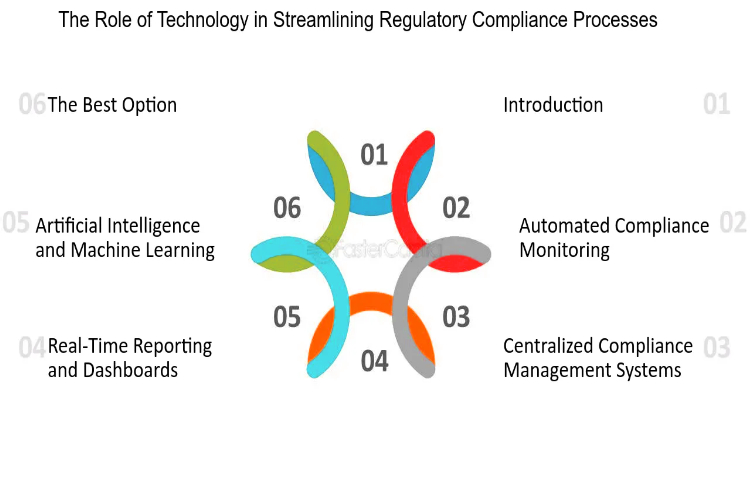
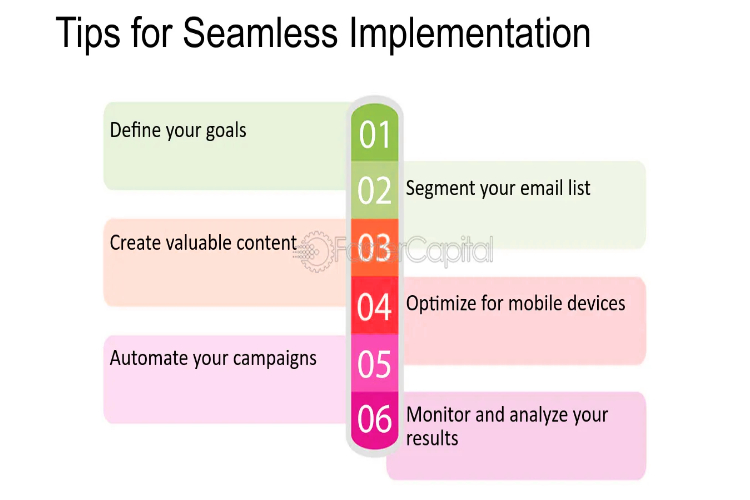
In the dynamic realm of securities trading, transparency stands as a cornerstone of trust and efficiency. As markets evolve and expand globally, the need for standardized systems to identify and track securities becomes increasingly paramount. Integrated Character Codes (ICCs) emerge as a solution to this challenge, promising to revolutionize the landscape by enhancing transparency and […]
Enhancing Transparency: The Impact of Integrated Character Codes on Securities Trading Read More »